DevSecOps

Introduction
Before the advent of DevOps, most organizations performed their products’ security checks at the final stages of the software development life cycle (SDLC), irrespective of the development model adapted. Since the focus was predominantly on application development, security was deemed to be less important at other stages. Security checks are performed very late in the development cycle. Often, the product would be almost fully developed. Hence, discovering a security threat at such a late stage meant a lot of rework leading to waste of resources.
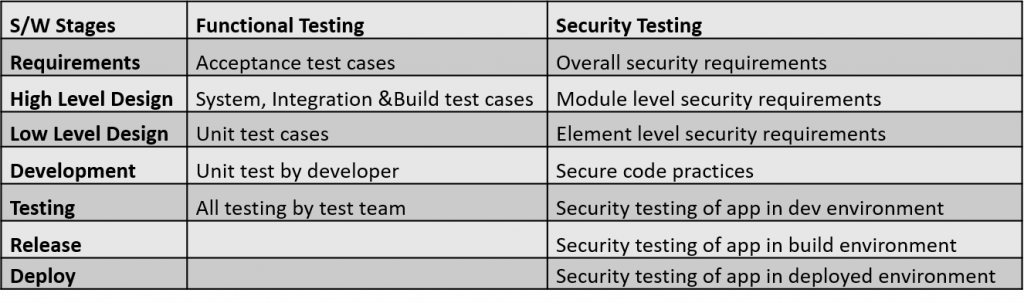
DevSecOps reduces the costs of fixing the security flaws by incorporating security into every stage of the development lifecycle, from the requirement stage to the operations stage.
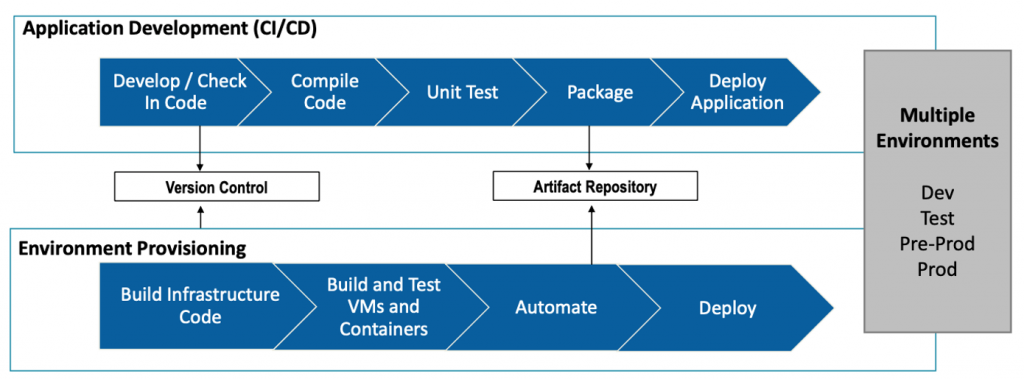
Implementing DevOps results in better collaboration between teams, faster time to market, improved overall productivity, which enhances customer satisfaction.
DevSecOps emphasizes everyone’s role in security. It injects security practices into an organization’s DevOps framework. The goal is to incorporate security into all stages of the software development workflow instead of leaving it to the final stages of the SDLC.
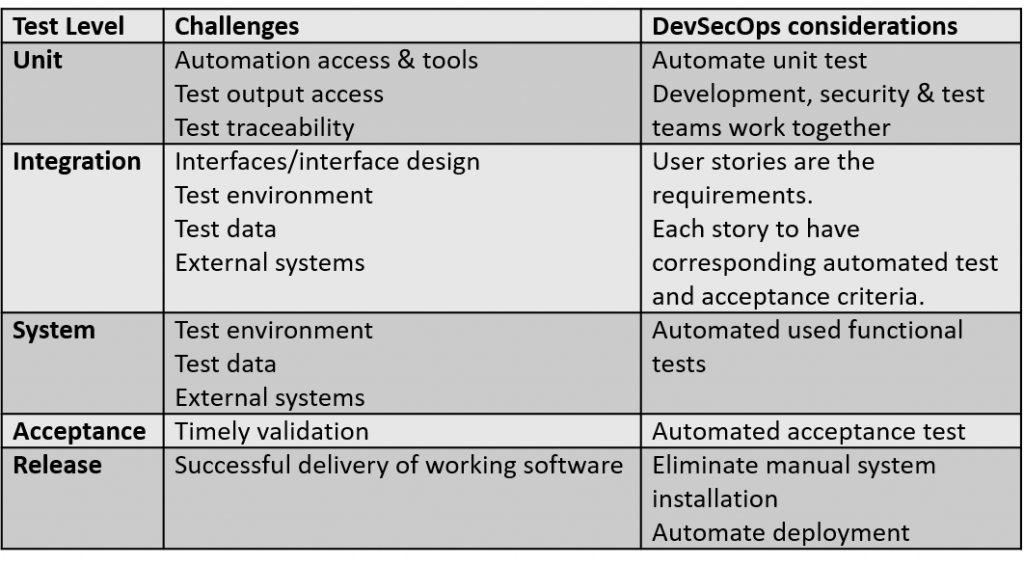
DevSecOps do not replace your development model like Agile, rather complements it. Instead, they complement each other to help the organization maximize its benefits. Agile fosters collaboration and constant feedback. Unlike Agile, DevSecOps encompasses the complete lifecycle of a software product till production. DevSecOps provides methodologies and tools to facilitate agile adjustments.
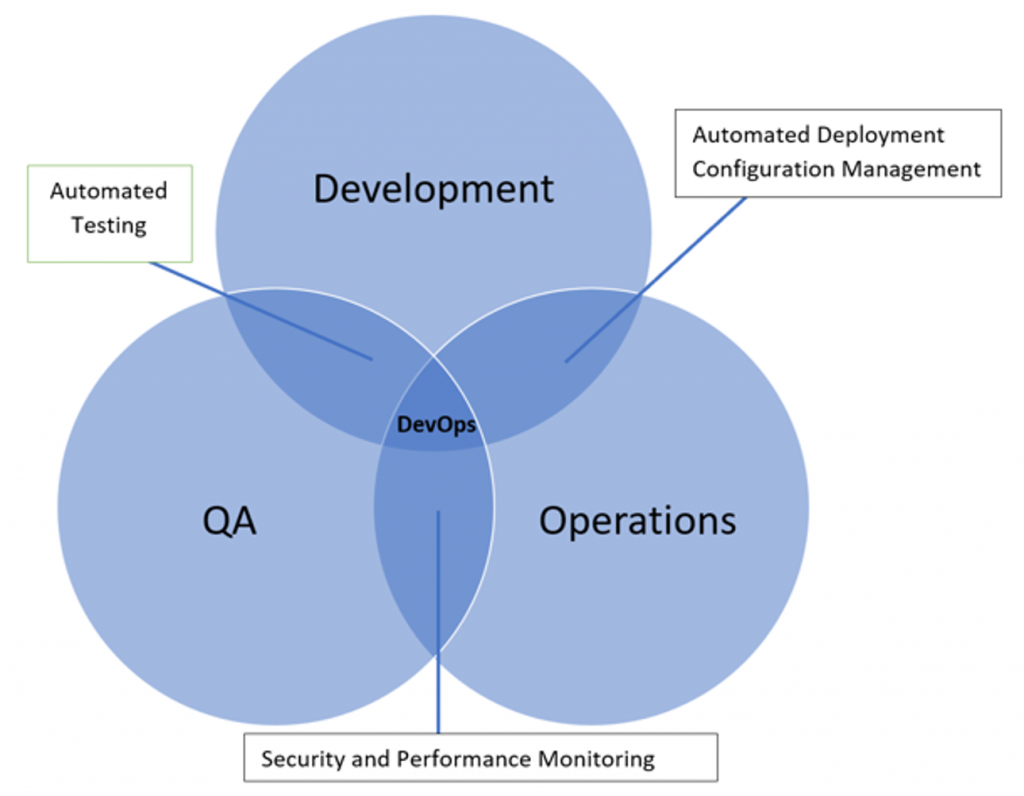
The value proposition of DevSecOps:
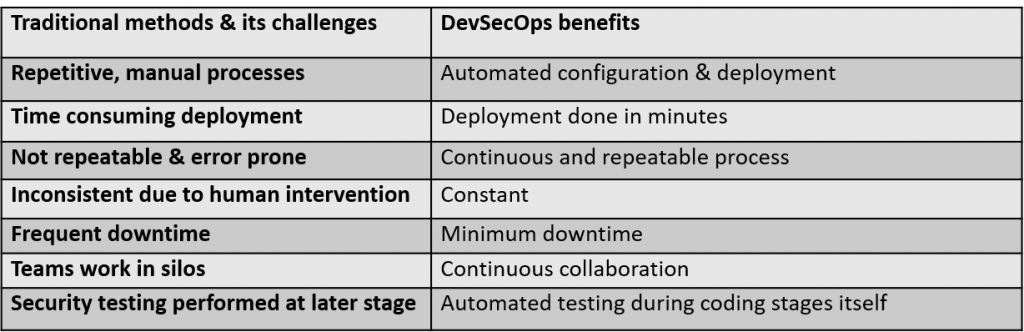
DevSecOps is the way forward for secure & efficient development as it improves the work culture & practices by bringing in automation across stages.