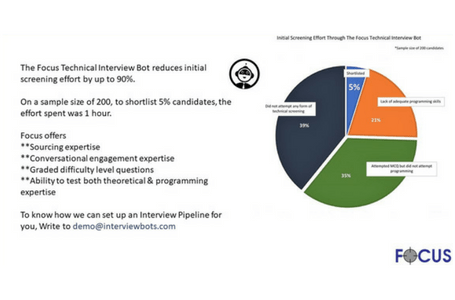
Data Ownership


Introduction
Let’s start with the most important question which many organizations face today – Who is responsible for implementing data protection??
You would be hearing various responses ranging from “it’s everybody’s job”, “it’s teamwork”, to “its business analysts’ responsibility” etc. In such a scenario where does the obligation rest?
In an ever-changing business / competitive world, the primary objective is a need for a “workable” or a “shippable” product. The various stakeholders have multiple expectations. The business wants it quick, CDO & CISO wants it to be compliant with regulations, management wants it to be cost-effective and better than their rivals’ products. Caught in between all these humongous expectations, compliance or adhering to the best practices can easily be overlooked by the team.
Given the lack of ownership or directions, it is going to be a hard-hitting task to have data compliance in the place, as there are multiple factors and stakeholders involved in the entire lifecycle. This tends to put the data governance fall into an “all alone” territory where neither the CISO nor the CDO or the compliance team would be made accountable.

The Way Ahead
One of the different ways to overcome the issue is to tag this responsibility to the product owner or the application owners who typically develop the systems. Obviously just assigning the task would not help improve the data security or governance. The teams must be truly cultured and trained on the need and the importance which would help them to practice this while developing products.
Given the nature of an agile development world, the data security implementation program should be taken up right from the early stages. This shall be sustained which gradually improves the compliance of the product and as well as the organization’s compliance posture.
Today’s business applications store transmits, and process a lot of data which in turn puts a serious challenge of data access to the right stakeholder. Many times root cause analysis would also point to a typical problem of “Sensitive Data being available to all users irrespective of the roles/privileges”
Lots of organizations deploys various process like DLP, end point security etc. to check this issue. The developer community also uses active directory for user authentication. The best practice does not stop here. In fact, it should reach to a traceability level where there is a provision of storing all the details of the activities which was done in the application by the user.
Data Security
Data security can be described as the process of protecting data from unauthorised access throughout the lifecycle. This can be done through data encryption, hashing, tokenization & key management practices. Leading global regulations recommend Pseudonymization or Encryption as an acceptable way for data protection. This would help solve a lot of problems during forensic investigations and comply to universal data regulations.

The following ways can also be looked upon by the project team for securing data:
Data encryption
Data masking
Data resilience
Conclusion:
A properly deployed data security framework which is practiced by the application owners should be subjected to various checks and balances. Investing in security training to the development team would be of tremendous help which would empower them to contribute in achieving the organization goal of reducing the organizational risk, but also improve the security posture of the organizations in various ways. The primary objective of the continually securing data across the Lifecyle and adhering to various compliance regulations across the globe is met in a seamless way.