Browser Forensics


When we say Digital Forensics, we mean the process by which we identify the crucial evidence, which is then extracted using various methods, and the same is preserved to be presented in the court of law, after proper documentation. This is a more of an art than science, in which we hunt for crucial electronic evidence from the various digital media present out there, from a computer, mobile, server to a network. Broadly, the novel techniques relating to e-mail, mobile, database, malware, disk and the browser forensics provide the investigating team with a variety of tools and provisions to collect crucial evidence and crack any tough case.
Web browsers are our eyes to the internet and everything that goes on in the internet mostly goes through the browsers leaving a whole lot of data behind, from cookies, history of websites surfed, downloaded files to the cached data, thereby providing a gold mine of information during a forensic investigation.

Web Browser as a Forensic Tool:
Before investigating the information of a user gathered by the web browser, it is crucial for us to understand the mechanism by which the web browser gathers the data initially and how it is subsequently stored in the computer.
Let us look at the progression of things here.
The user enters the website name, the URL onto the browser’s address bar or searching for the same using keywords in a search engine.
The URL is then searched by the web browser, and is subsequently located and connected to, by breaking it into an IP address, which makes the URL unique and that the user is kept from connecting to the wrong website.
While the above process happens, the web browser is also simultaneously creating log files, storing data onto the cache files and a few other things in the user’s device.
Browsers Artifacts:
By browser artifacts we are referring to the navigation history, bookmarks, downloaded file list, cache data, and various other things, that are stored inside specific folders in the user’s local computer. This varies from browser to browser, and are stored in different names, but are mostly standard across versions for a single browser and they all store the same type of data.
Let us look at some of the common artifacts stored by browsers.
Web History: This section of the browser stores all the websites visited by the user. This could be used to check if the user has surfed some malicious websites or get information on his usage pattern.
Autofill/Autocomplete and Form Data: Whenever user visits a website and fills in information in the search box or in an online textbox or a form, it is stored by the browser sometimes with the knowledge of the user and sometimes without. This information could be used in relation to the web history of the user to get solid insights.
Bookmarks: This is the list of websites that the user has willingly bookmarked and stored.
Extensions, plugins and Addons: This is specific to the browser and can give a lot of insights on the user’s activity.
Cache: When navigating websites, the browser creates all sort of cache data (images, JavaScript files) for many reasons. For example, to speed loading time of websites. These cache files can be a great source of data during a forensic investigation.
Logins: These are crucial as the user keys in the login credentials and some might be accepted by the user to be stored with the browser.
Favicons/thumbnails: These are tiny little icons and images that are mostly loaded as the icons that go with the websites, mostly company logos. These are stored in the browser and could contain key information on the websites visited by the user.
Browser Sessions: These are the time logs given in the web history and could give information on the timings of web surfing by the user.
Downloads: This is the list of files downloaded by the user. Ctrl + J is mostly the default shortcut for getting to this list in most of the browsers.
We have covered almost all crucial components of the browser with respect to getting vital forensic inputs during an investigation. Let us move over to how and where to recover them from, if they were deleted before the investigation.
4 key recovery methods to recover deleted browser history:
Through cookies
Cookies that are stored by the browser is another way to get to the web history of the user. We are talking about a tiny text file that gets stored in the browser. Use a third-party software to open them and view history.
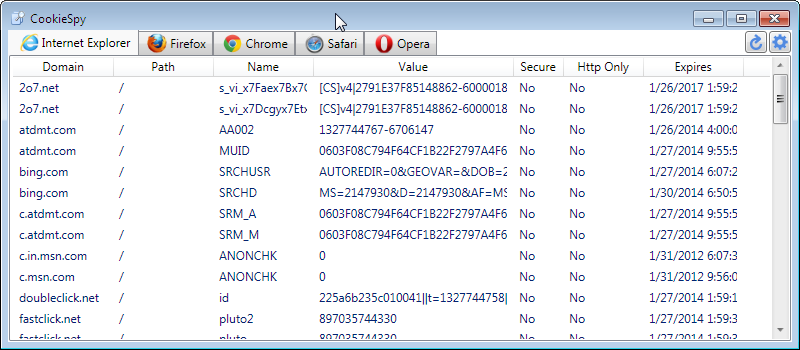
The below method could be used to recover deleted cookies (through System Restore).
When the data relating to the browser that is stored is deleted, there is still a possibility that a periodic system restore has happened recently and a restoration point is available in the operating system to go back to. This would mean that we can get the deleted files back, but only dating back from the date and time at which the restoration point is created. This is specific to the Windows OS.
Go to the Start menu and type System Restore to get to the Recovery window under Control Panel and you can restore the system back to a previous restoration point using the Open System Restore option. Once the restoration is done and the computer is restarted, you should now have access to all the deleted files, of course from before the date of the restoration point.
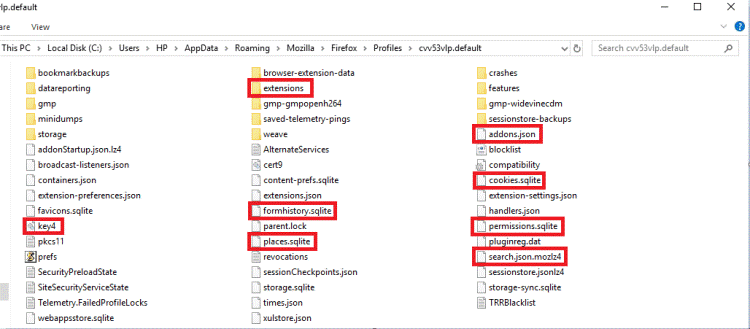
Access deleted browsing history with log files
By using this method, you can recover the history using the log files that are stored in the user’s computer and you could use this method if you are looking to recover the file that has been deleted a while back. This is done by getting access to the hidden index.dat file that is stored in the local computer that contains the web history of the user. You can also use a third-party file recovery software to get back the deleted data. You can look to recover the following information out of this: –
- The web history including information on redirects and the count on how many times the user has visited a particular website.
- Information on bookmarks created by the user.
- One can look for files in the default “Downloads” directory or any other directory to which the downloads are possibly moved. This could be tracked using the file names download list.
- Cookies that give you web history as said before.
- Cache files that once again, store web history and relevant information temporarily, but on user’s local computer.
Through Google History
This is another alternative place where the user’s web history is stored together with the timestamps. The user’s web history is usually stored in the browser, but if the user has chosen to log into multiple devices using his Google id then his surfing pattern, web history and the searches are, by default, stored by Google in the “Activity” section.
If you want to look at the web history of the user, you can access the same by going to activity.google.com. This information is available even when the user deletes the web history from his browser(s), but there is a catch. For the user’s web-history to be available in his activity.google.com, he should have not paused this logging by Google, which is on by default.
If at any time any Google user does not want his history to be logged in at activity.google.com, he has the option to pause the same. The Google user can also selectively delete his web history that is available in the activity section. One more catch is that you have to be signed in as the user to get access to this information from the activity.google.com website.
Through DNS Cache
This method works only when the computer is on and is connected to the internet and is by-far the fastest method to restore the web-history. Open the Command prompt and type in ipconfig/displaydns and then hit enter. This will give a wall of text which will take time to stop if there are many websites to display. You can scroll up and check this out once the display lists everything and stops.
Tool List:
Browsing history View, IE Cookies View, IE History View, IE Cache View, Mozilla Cookies View, Mozilla History View, Mozilla cache view, Opera cache view, Chrome cache view, Chrome history view, Safari History View, Safari Cache View, My Last Search, Website sniffer V1.00, Firefox Downloads view
Challenges in Browser Forensic Process:
- The user has a habit of surfing internet not in one, but multiple browsers, in which case components and files of all these browsers are to be checked.
- As mentioned earlier, various browsers use various storage mechanisms and location to store these files and that need to be taken care here.
- As new versions of browsers come out new modalities of storing these browser-based information are employed. The locations will remain mostly the same but the change if any are to be noted. They might not be the same as where the browsers started in their first version.
- The usage of various nonstandard browsers is a huge obstacle in an investigation. This is mostly the weapon of choice by the adversaries to obfuscate their activities.
Conclusion:
The field of Digital Forensics is spreading its wings with new tools coming in everyday, making the job of the investigator easier and efficient. Forensics, especially digital forensics is an arena where the investigators take great care in handling the data, starting from the extraction of the data till presenting the same in the court of law, the information is considered highly delicate and preserving the same in its original untouched form is always paramount to the case at hand.
We have new frameworks emerging to handle digital forensic information and the arena is only poised towards getting more organized in the coming days, with new technologies and methodologies in handling usage data.